Detect Unknown and Insider Threats
Ready to uplevel your analysts and reduce noise? Securonix User and Entity Behavior Analytics (UEBA) uses the power of machine learning and artificial intelligence to baseline behavioral patterns and uncover anomalous activity with minimal noise.
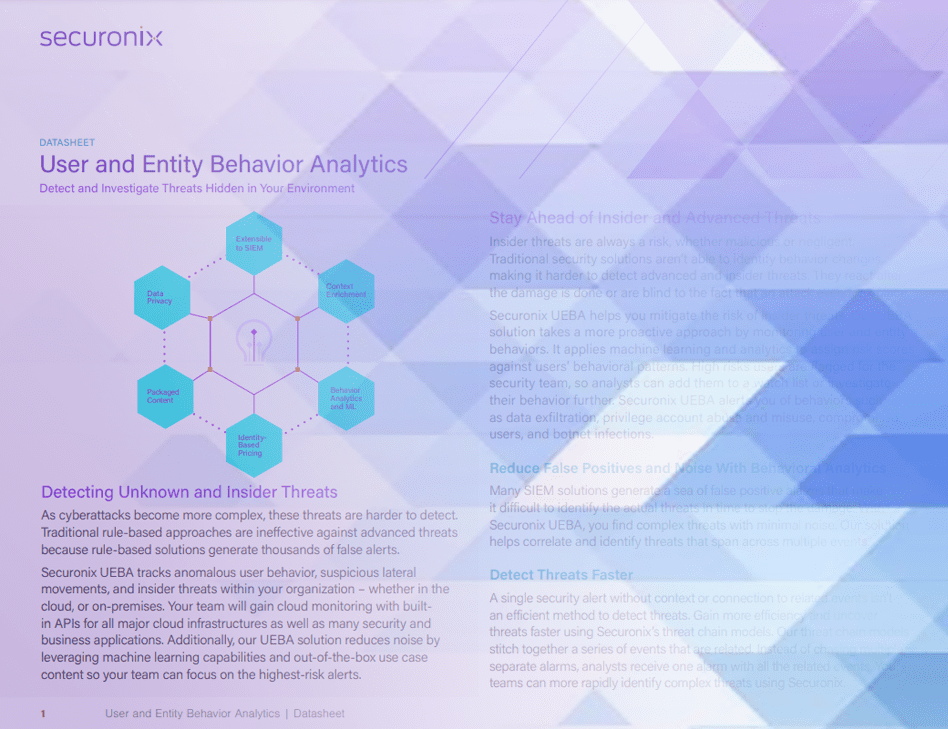
Data Privacy by Design
We put privacy first by enforcing role-based access controls, masking user data, and encrypting data both in transit and at rest. In compliance with GDPR we also offer detailed logging for a full audit trail of activities.
Real-time Entity Context
Transform raw events into meaningful insights in real-time with entity context. Security alerts are enriched with information around user identity, assets, network activities, and geo-location to give you a complete picture of risk in your organization.
Packaged Content Applications
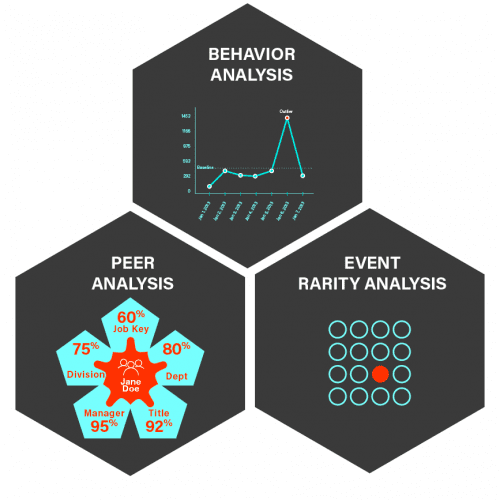
Benefit from immediate, one-click access to out-of-the-box content for common use cases such as: insider threat, cyber threat, fraud, cloud security, and business applications.
ML Based Behavior Analytics
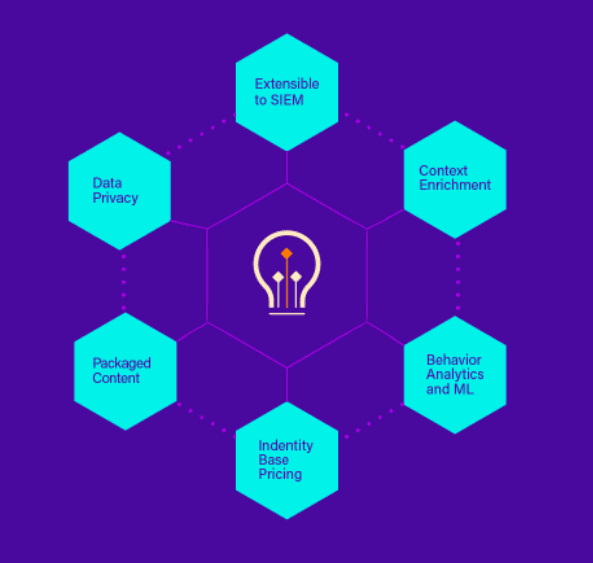
Leverage behavioral analytics to accurately detect advanced and insider threats. Using threat chain models you can stitch together a series of events to surface the highest risk alerts and prioritize low and slow threats.
Read the Data Sheet
User and Entity Behavior Analytics
Securonix User and Entity Behavior Analytics (UEBA) leverages sophisticated machine learning and behavior analytics to analyze and correlate interactions between users, systems, applications, IP addresses, and data. Light, nimble, and quick to deploy, Securonix UEBA detects advanced insider threats, cyber threats, fraud, cloud data compromise, and non-compliance. Built-in automated response playbooks and customizable case management work flows allow your security team to respond to threats quickly, accurately, and efficiently.
Why the Securonix Platform?
Detection
Detect Unknown Threats
Threat Chains: Identify low and slow attacks with threat models that map to both the MITRE ATT&CK and US-CERT frameworks.
Time-to-Value
Realize Fast Time-to-Value
Turnkey Analytics: Investigate and respond more efficiently with built-in analytics, connectors, and case management workflows.
ROI
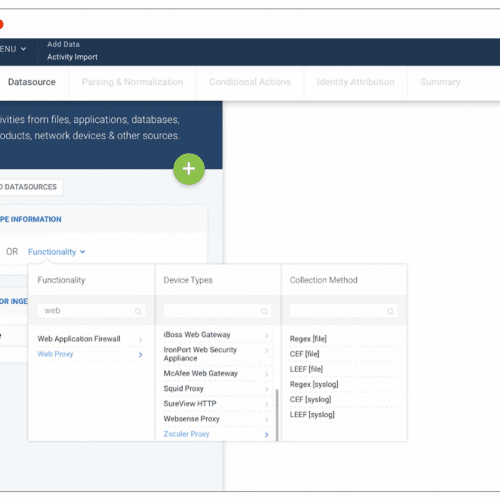
Maximize Your SIEM Investment
SIEM + UEBA: Realize cost savings on your existing investments by seamlessly integrating our UEBA with any other legacy SIEM. Cloud-Native: Our platform allows you to benefit from all the data in your IT environment with zero infrastructure to manage.
Read The Whitepapers
Stay Ahead of Insider Threat Trends
Learn what the Securonix Threat Research Team discovered when they analyzed hundreds of real-world insider threat incidents. Management report.
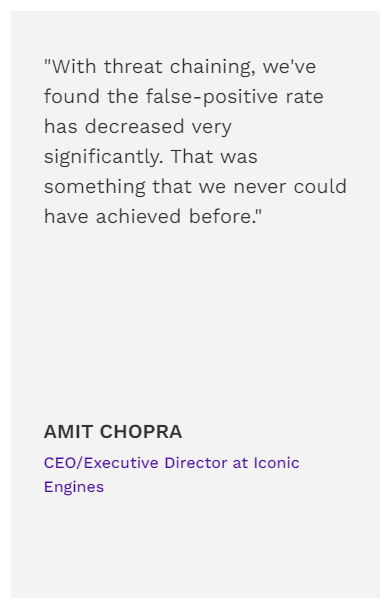
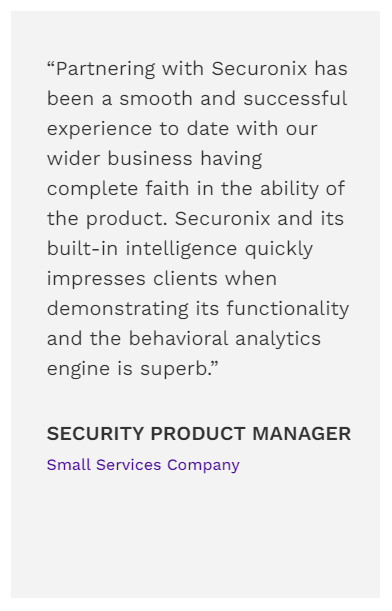
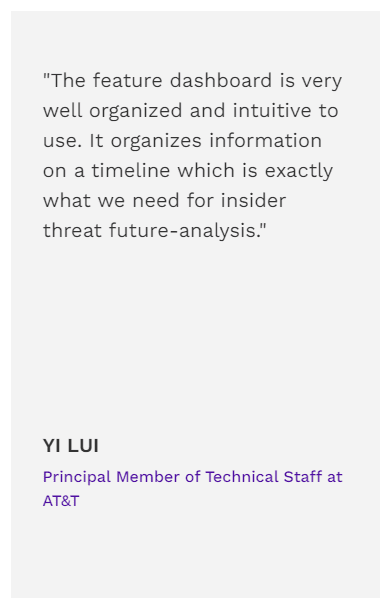
Testimonials
If you would like more information on Securonix, contact us today!